Clean • Professional
When applications communicate with other applications — without any logged-in user involved — they still need a secure and reliable way to authenticate. That’s where the OAuth2 Client Credentials Flow plays a crucial role.
If you're building microservices, backend APIs, service-to-service integrations, or automated jobs, understanding this flow is essential for implementing secure and scalable authentication.
In this guide, we’ll break down the concept in a simple, easy-to-understand, and practical way so students and developers can confidently apply it in real-world projects.
The OAuth2 Client Credentials Flow is an authorization flow designed for scenarios where no end user is involved.
It is commonly used when:
Instead of authenticating a user, the client application authenticates itself using:
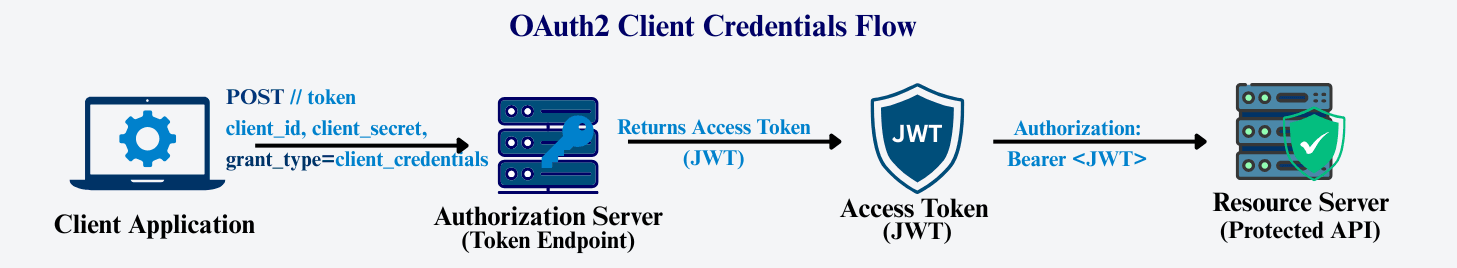
client_idclient_secretAfter successful authentication, the Authorization Server issues an access token. The client then uses this token to securely call protected APIs.
You should use this flow in situations where services communicate directly without user interaction, such as:
This flow is not suitable for user login scenarios. If your application involves authenticating users (like web or mobile apps), you should use the Authorization Code Flow instead.
Let’s break it down simply.
Step 1: Client Authenticates Itself
The client application sends a request to the Authorization Server with:
client_idclient_secretgrant_type=client_credentialsExample HTTP request:
POST /oauth/token
Content-Type: application/x-www-form-urlencoded
grant_type=client_credentials&
client_id=my-client&
client_secret=my-secret
Step 2: Authorization Server Issues an Access Token
If the client credentials are valid, the Authorization Server responds with an access token:
{
"access_token": "eyJhbGciOiJSUzI1NiIsInR5cCI6IkpXVCJ9...",
"token_type": "Bearer",
"expires_in": 3600
}
This access token is usually a JWT.
Step 3: Client Calls the Protected API
The client now uses the access token to call a secured API.
It includes the token in the HTTP header:
Authorization: Bearer <access_token>
The Resource Server validates the token before granting access.
The Client Credentials Flow has some distinct characteristics that make it ideal for backend and service-to-service communication:
This flow is formally defined under the OAuth 2.0 specification.
OAuth2 provides different flows for different authentication needs.
Each flow is designed for a specific use case. Choosing the right one keeps your application secure and scalable. Some flows are meant for user login, while others are built for service-to-service communication.
Authorization Code Flow
Best for: Applications where users log in with accounts.
Client Credentials Flow
Best for: Service-to-service or machine-to-machine authentication.
Resource Owner Password Flow
Best for: Legacy systems only (not recommended for new applications).
Device Code Flow
Best for: Devices that cannot easily display login forms.
Spring Boot makes it easy to implement the Client Credentials Flow using:
Add the following configuration:
spring:
security:
oauth2:
client:
registration:
my-client:
client-id: my-client
client-secret: my-secret
authorization-grant-type: client_credentials
scope: read
provider:
my-provider:
token-uri: <https://auth-server/oauth/token>
Now you can use WebClient to call a protected API.
Example:
@Bean
public WebClient webClient(WebClient.Builder builder) {
return builder.build();
}
When properly configured, Spring automatically:
Authorization: Bearer <token> headerYou don’t need to manually fetch or attach tokens.
client_secret in frontend or browser-based applicationsThe Client Credentials Flow is widely used in:
It plays a critical role in enabling secure and scalable machine-to-machine authentication.
In a zero-trust architecture:
The Client Credentials Flow aligns well with this model because it:
The OAuth2 Client Credentials Flow is essential for secure backend communication. It enables stateless, scalable service-to-service authentication without involving users.
Understanding this flow helps you build secure APIs and microservices using OAuth 2.0 principles.