Clean • Professional
CORS (Cross-Origin Resource Sharing) is a browser security mechanism that controls which domains are allowed to access your backend APIs.
In Spring Boot, CORS configuration becomes essential when your frontend and backend run on different origins.
CORS is a browser security feature that restricts web pages from making requests to a different origin than the one that served the page.
An origin is defined by:
Example:
http://localhost:3000 (React / Angular)http://localhost:8080 (Spring Boot)👉 These are different origins, so the browser blocks requests unless CORS is configured.
Without proper CORS configuration:
Required for:
Blocked by CORS policyNo 'Access-Control-Allow-Origin' headerPreflight request failedThese errors occur when CORS rules are missing or misconfigured.
Frontend(Browser)
|
| HTTP Request
v
BackendAPI(SpringBoot)
|
| CORS Check
v
Allowed?──YES→Responsesent
└─NO→Browserblocksrequest
CORS (Cross-Origin Resource Sharing) is a browser security feature that controls which websites can access your backend APIs. Understanding CORS is essential for avoiding errors and configuring your Spring Boot applications correctly.
A Simple Request is the easiest type of cross-origin request. It does not trigger a preflight (OPTIONS) request.
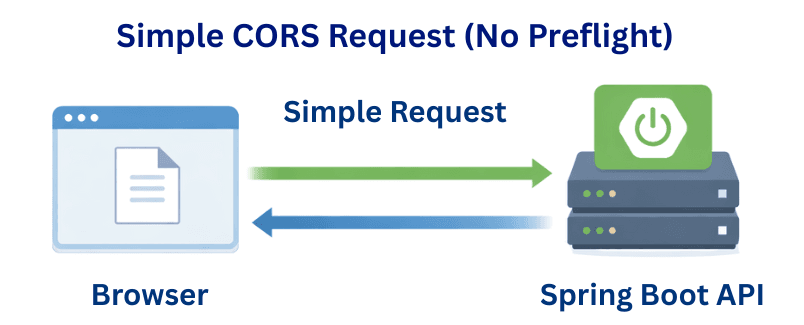
application/x-www-form-urlencoded, multipart/form-data, text/plain)application/x-www-form-urlencodedmultipart/form-datatext/plainHow It Works
Browser → Direct API Request → Spring Boot API → Responsewith CORS headers → Browser
Example: Simple GET Request
GET /api/users
Origin: <http://localhost:3000>
Access-Control-Allow-OriginSpring Boot Example
@CrossOrigin(origins = "<http://localhost:3000>")
@GetMapping("/users")
public List<User>getUsers() {
return userService.getAllUsers();
}
A Preflight Request is triggered when the browser needs to check permissions before sending the actual request.
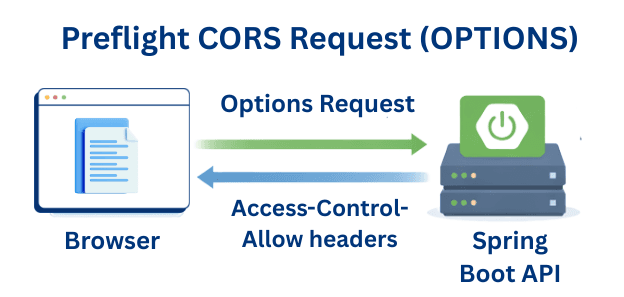
When Preflight Happens
application/jsonFlow of Preflight Request
Browser →OPTIONS Request (Preflight) → Spring Boot API →Access-Control-Allow-* headers → Browser → Actual API Request → Spring Boot API
Example: Preflight OPTIONS Request
OPTIONS /api/users
Origin: <http://localhost:3000>
Access-Control-Request-Method: PUT
Access-Control-Request-Headers:Authorization
Spring Boot Configuration for Preflight
registry.addMapping("/**")
.allowedOrigins("<http://localhost:3000>")
.allowedMethods("GET","POST","PUT","DELETE","OPTIONS")
.allowedHeaders("*");
Credentialed Requests include cookies, sessions, or authorization tokens.
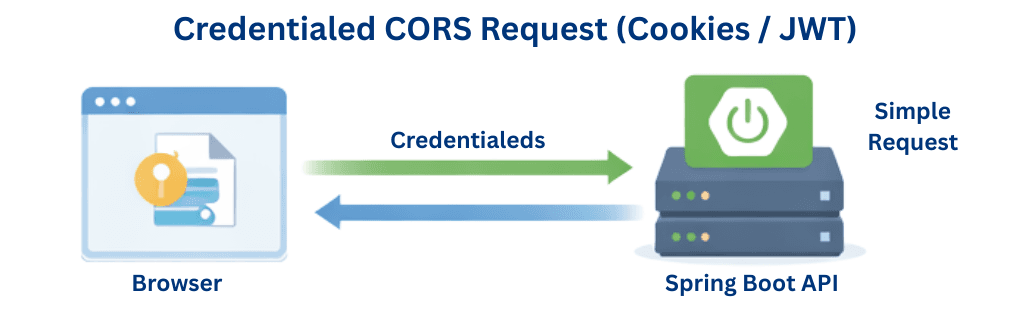
Examples
Rules for Credentialed Requests
allowedOrigins("*") cannot be usedFlow
Browser (with cookies/token) → CORS Requestwith Credentials → Spring Boot API →Access-Control-Allow-Credentials:true → Browser
Spring Boot Example
registry.addMapping("/**")
.allowedOrigins("<http://localhost:3000>")
.allowedMethods("*")
.allowedHeaders("*")
.allowCredentials(true);
Non-Simple Requests are complex requests that trigger a preflight.
When Requests Are Non-Simple
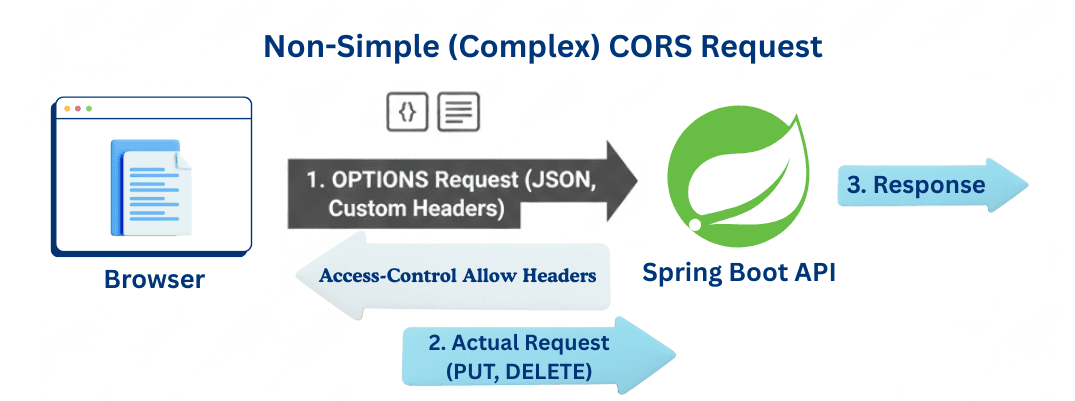
Example
application/jsonEssentially, Non-Simple Requests = Preflight Request + Actual Request
CORS (Cross-Origin Resource Sharing) allows your frontend applications to access backend APIs safely. In Spring Boot, there are multiple ways to configure CORS depending on your project size and requirements.
1. @CrossOrigin (Controller or Method Level)
This approach is best for small projects or specific APIs.
@CrossOrigin(origins = "<http://localhost:3000>")
@RestController
@RequestMapping("/api/users")
publicclassUserController {
@GetMapping
public List<User>getUsers() {
return userService.getAllUsers();
}
}
Features:
2. Global CORS Configuration
For REST APIs and production applications, a centralized CORS setup is recommended.
@Configuration
publicclassCorsConfigimplementsWebMvcConfigurer {
@Override
publicvoidaddCorsMappings(CorsRegistry registry) {
registry.addMapping("/**")
.allowedOrigins("<http://localhost:3000>")
.allowedMethods("GET","POST","PUT","DELETE","OPTIONS")
.allowedHeaders("*")
.allowCredentials(true);
}
}
Benefits:
3. CORS with Spring Security
If your application uses Spring Security, you must configure CORS inside the security setup, otherwise requests may still fail.
Security Configuration Example
@Bean
public SecurityFilterChainsecurityFilterChain(HttpSecurity http)throws Exception {
http
.cors()
.and()
.csrf().disable()
.authorizeHttpRequests()
.anyRequest().authenticated();
return http.build();
}
CorsConfigurationSource Example
@Bean
public CorsConfigurationSourcecorsConfigurationSource() {
CorsConfigurationconfig=newCorsConfiguration();
config.setAllowedOrigins(List.of("<http://localhost:3000>"));
config.setAllowedMethods(List.of("GET","POST","PUT","DELETE"));
config.setAllowedHeaders(List.of("*"));
config.setAllowCredentials(true);
UrlBasedCorsConfigurationSourcesource=newUrlBasedCorsConfigurationSource();
source.registerCorsConfiguration("/**", config);
return source;
}
allowedOrigins("*") in production| CORS Configuration Method | Scope | Best Use Case | Advantages | Limitations |
|---|---|---|---|---|
@CrossOrigin Annotation | Controller / Method level | Small projects, single APIs | Very easy to use, quick setup | Not scalable, repetitive for large apps |
Global CORS (WebMvcConfigurer) | Application-wide | REST APIs, production apps | Centralized, clean, maintainable | Does not work alone with Spring Security |
| Spring Security CORS Config | Application-wide (Security layer) | Secured APIs with authentication | Works with tokens, cookies, sessions | Slightly complex setup |
CORS configuration in Spring Boot is mandatory when your frontend and backend are on different origins.