Clean • Professional
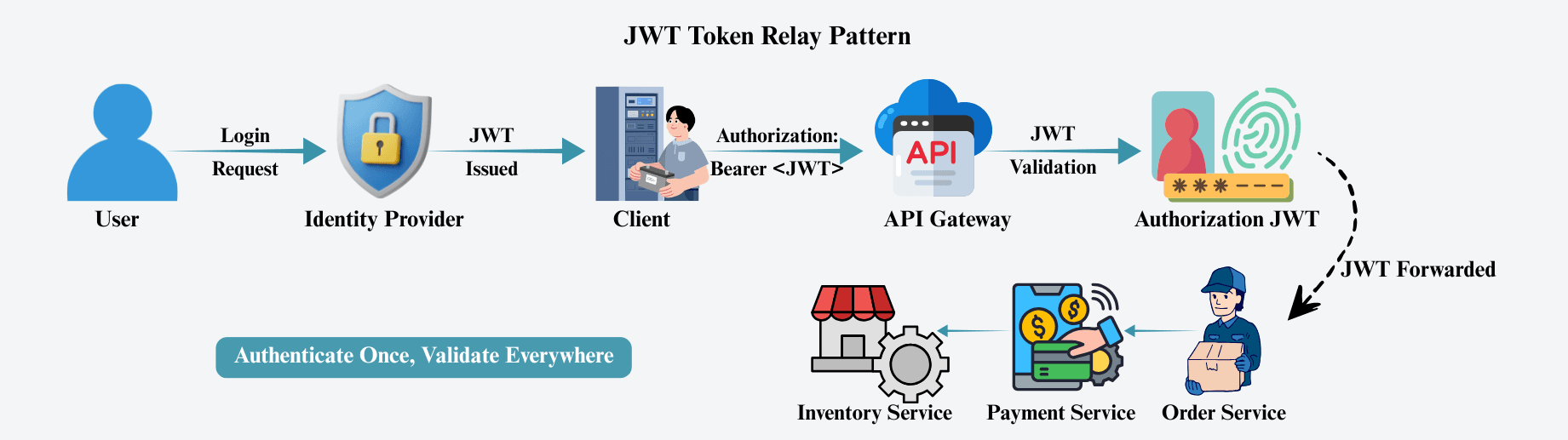
In modern distributed systems, authentication is only half the story. The real challenge is identity propagation — once a user logs in, how do downstream services like Order, Payment, or Inventory know who actually initiated the request?
This is where the JWT Token Relay Pattern becomes essential.
If you're building production-ready Spring Boot microservices, understanding this pattern is not optional — it’s a core security concept every backend developer should master.
The JWT Token Relay Pattern is a design approach where a JSON Web Token (JWT) issued after authentication is forwarded (relayed) from one service to another during internal service communication.
Instead of each microservice calling the Identity Provider repeatedly:
Authorization header.In simple words:
Authenticate once. Validate everywhere.
This enables:
Without token relay, internal services only know that another service made the request — not which user initiated it.
This creates problems such as:
Token Relay fixes this by preserving the original user identity throughout the entire request chain.
Modern systems are built using:
Traditional session-based authentication introduces scalability bottlenecks and tight coupling. JWT-based authentication removes these issues, and Token Relay ensures identity consistency across distributed services.
The client authenticates using OAuth 2.0 or OpenID Connect.
The Identity Provider issues a signed JWT containing:
iss)aud)exp)The client sends the request:
Authorization: Bearer <access_token>
The API Gateway:
If valid, the request is forwarded.
When the Gateway calls internal services:
No additional login request is required.
Identity securely flows across the entire microservices chain.
Spring makes implementation straightforward using:
Step 1: Configure Token Relay in Spring Cloud Gateway
You can enable token relay directly in application.yml:
spring:
cloud:
gateway:
routes:
- id: order-service
uri: lb://order-service
predicates:
- Path=/orders/**
filters:
- TokenRelay=
The TokenRelay filter:
No custom Java code required for basic relay.
Step 2: Configure Microservice as Resource Server
Each microservice must validate the JWT independently.
Example configuration:
@Configuration
@EnableWebSecurity
public class SecurityConfig {
@Bean
public SecurityFilterChain filterChain(HttpSecurity http) throws Exception {
http
.authorizeHttpRequests(auth -> auth
.requestMatchers("/orders/**").hasAuthority("SCOPE_read")
.anyRequest().authenticated()
)
.oauth2ResourceServer(oauth2 -> oauth2
.jwt(Customizer.withDefaults()));
return http.build();
}
}
This ensures:
Each service trusts the JWT signature — not the calling service.
For production-grade systems:
Even internal networks must follow zero-trust principles.
JWT Token Relay
Token Exchange
For most projects and real-world systems, JWT Token Relay is sufficient.
Use JWT Token Relay if:
It may not be necessary for monolithic or session-based legacy systems.
JWT Token Relay is widely used in:
It forms the backbone of identity-aware distributed systems.
The JWT Token Relay Pattern is essential for building secure and scalable Spring Boot microservices. It ensures that user identity flows securely from the API Gateway to every downstream service without relying on centralized session storage or repeated authentication calls.
By combining:
You can build a secure, scalable, and production-ready microservices ecosystem that follows modern cloud-native and stateless architecture principles.