Clean • Professional
Spring Security offers two of the most commonly used authentication methods: Form-Based Login and HTTP Basic Authentication. Understanding their differences, setup, and best practices is essential for developers building secure Spring Boot web apps or REST APIs.
Form Login allows users to authenticate using a custom login page. It’s ideal for web applications with user interfaces.
/login by default).AuthenticationManager validates credentials using:
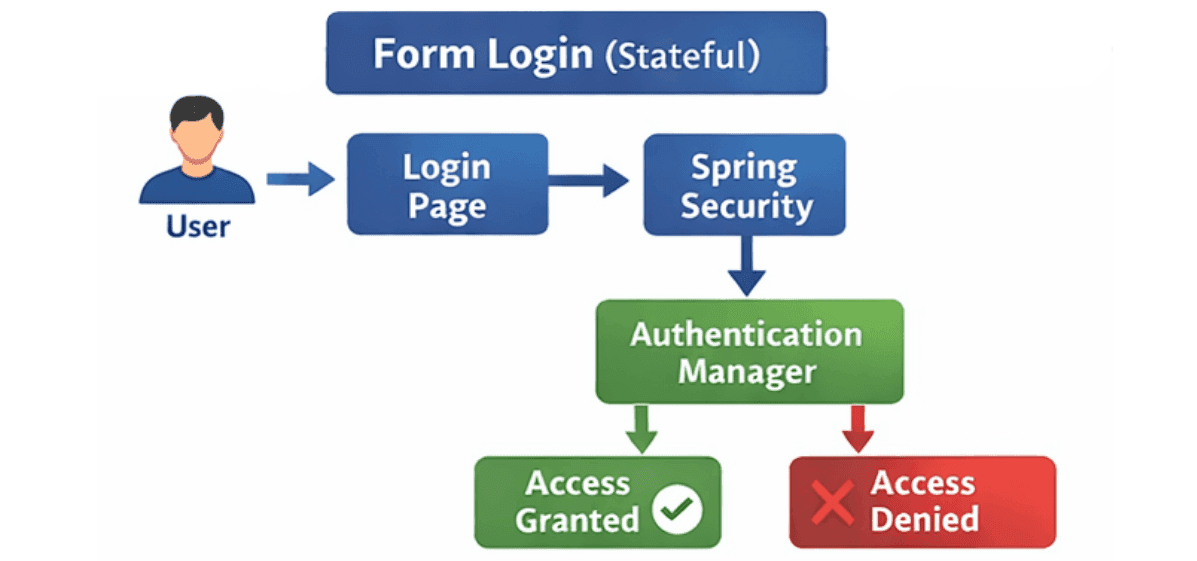
Example: Form Login Configuration
@Configuration
@EnableWebSecurity
publicclassSecurityConfig {
@Bean
public SecurityFilterChainfilterChain(HttpSecurity http)throws Exception {
http
.authorizeHttpRequests(auth -> auth
.requestMatchers("/admin/**").hasRole("ADMIN")
.anyRequest().authenticated())
.formLogin(form -> form
.loginPage("/login")// Custom login page
.defaultSuccessUrl("/home")// Redirect on success
.failureUrl("/login?error")// Redirect on failure
.permitAll())
.logout(logout -> logout
.logoutUrl("/logout")
.logoutSuccessUrl("/login?logout")
.permitAll());
return http.build();
}
}
Advantages of Form Login
HTTP Basic Authentication is a stateless, header-based mechanism commonly used for REST APIs or microservices.
401 Unauthorized and WWW-Authenticate header.AuthenticationManager validates credentials.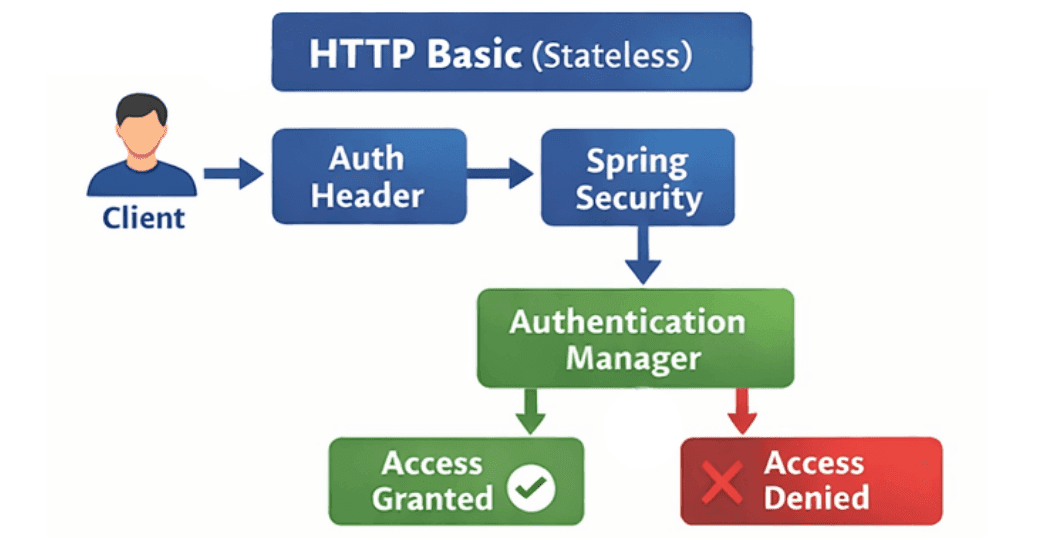
Example: Basic Authentication
@Configuration
@EnableWebSecurity
publicclassSecurityConfig {
@Bean
public SecurityFilterChainfilterChain(HttpSecurity http)throws Exception {
http
.authorizeHttpRequests(auth -> auth
.requestMatchers("/api/admin/**").hasRole("ADMIN")
.anyRequest().authenticated())
.httpBasic(Customizer.withDefaults())// Enable HTTP Basic
.csrf(csrf -> csrf.disable());// Disable CSRF for APIs
return http.build();
}
}
Advantages
Limitations
Spring Security uses UserDetailsService to load user-specific data (username, password, roles) from a chosen source.
Example:
@Service
publicclassCustomUserDetailsServiceimplementsUserDetailsService {
@Override
public UserDetailsloadUserByUsername(String username)throws UsernameNotFoundException {
// Load user from DB, LDAP, or in-memory
}
}
| Feature | Form Login | HTTP Basic Authentication |
|---|---|---|
| User Interface | Custom login page with form fields for username and password | Browser-generated login popup; no custom UI |
| State | Stateful (session-based authentication; user session stored on server) | Stateless (no session; credentials sent with every request) |
| Use Case | Ideal for web applications with a user interface | Ideal for REST APIs, microservices, or stateless services |
| Security | Supports CSRF protection, remember-me functionality, and session management | Credentials must always be sent over HTTPS to prevent interception |
| Flexibility | High – supports custom pages, success/failure handlers, and session management | Low – header-based only, minimal customization |
Spring Security provides flexible ways to authenticate users, supporting multiple sources depending on your application needs.
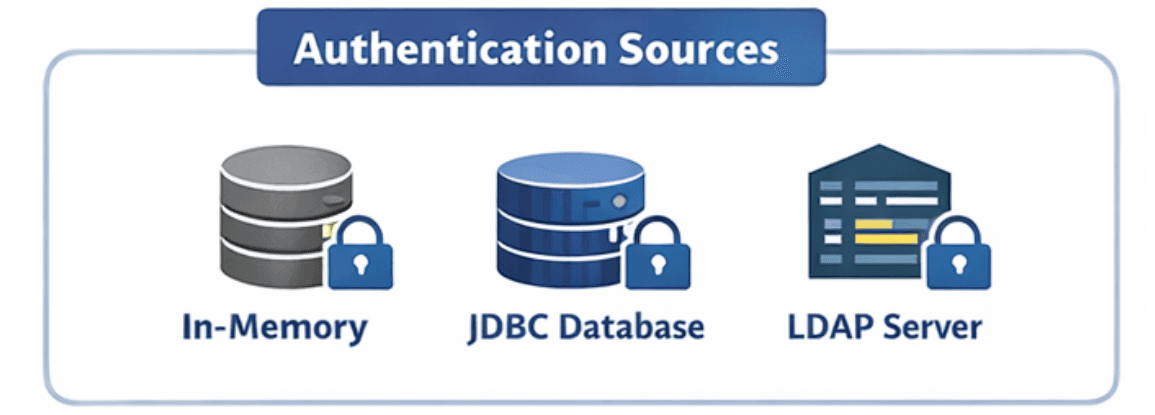
Storing passwords in plain text is unsafe. Spring Security requires strong password encoding.
| Password Encoder | Use Case |
|---|---|
BCryptPasswordEncoder | Default, secure for most applications |
Argon2PasswordEncoder | High-security requirements, resistant to modern attacks |
Form Login and HTTP Basic Authentication are foundational methods in Spring Security. By mastering them, developers can: